Today I talk about breaking into your first Info Sec job and things to do to stand out from the crowd. I also talk about the latest news about the Ethereum upgrade coming up in October.
Podcast: Play in new window | Download
Subscribe: RSS

Hack the planet!
Today I talk about breaking into your first Info Sec job and things to do to stand out from the crowd. I also talk about the latest news about the Ethereum upgrade coming up in October.
Podcast: Play in new window | Download
Subscribe: RSS
Cyber:
https://www.tripwire.com/state-of-security/latest-security-news/air-canada-mobile-app-breach/#.W4bIqojykj0.twitter
https://www.databreachtoday.com/breach-reveal-pge-exposed-30000-sensitive-records-a-11429?rf=2018-08-29_ENEWS_SUB_DBT_Slot1&mkt_tok=eyJpIjoiTkdRd09UUTJZak15WmpNMiIsInQiOiJkTEZOK0pNRU42YlpRMElJSHduZENaUVBoTmdBU0FndGl6TjFaaWR4dUxYNkZoSFwvd0FDU3A4R0lnTEdHYnoyQ1A0NnNUMjNMS2NQSmVxbjdTMndDeTM5Q0FrQTN3V2tjbHlseDhPUDBMT09uUnpVMXRwVmVpUzR6ZUJoXC91RUFlIn0%3D
Crypto:
https://www.ccn.com/bitcoin-accepted-everywhere-square-wins-patent-for-cryptocurrency-payment-network/
https://www.ccn.com/eos-price-jumps-on-referendum-system-proposal-gains-55-in-7-days/
https://www.ccn.com/eos-searches-for-solutions-as-ram-exploit-plagues-users/
Follow me on Twitter: @eenglish34
https://itunes.apple.com/us/podcast/cyber-security-cryptocurrency-podcast-with-eric-english/id1414720078?mt=2#
Podcast: Play in new window | Download
Subscribe: RSS
Cyber:
https://thehackernews.com/2018/08/windows-zero-day-exploit.html
https://www.engadget.com/2018/08/28/twitter-suspends-accounts-for-coordinated-manipulation/
https://krebsonsecurity.com/2018/08/fiserv-flaw-exposed-customer-data-at-hundreds-of-banks/
https://www.zdnet.com/article/why-facebook-is-powerless-to-stop-its-own-descent/
Crypto:
https://www.coindesk.com/openfinance-launches-regulated-trading-platform-for-security-tokens/
https://www.coindesk.com/above-7k-bitcoin-price-pushes-higher-in-break-past-resistance/
https://ripple.com/insights/the-inherently-decentralized-nature-of-xrp-ledger/
https://www.securityweek.com/hackers-breach-cryptocurrency-platform-atlas-quantum
Follow me on Twitter: @eenglish34
https://itunes.apple.com/us/podcast/cyber-security-cryptocurrency-podcast-with-eric-english/id1414720078?mt=2#
Podcast: Play in new window | Download
Subscribe: RSS
We have all started using hosted email and other cloud based applications in the IT realm. With Office365 there are a few things to consider doing to help harden and better secure your Office365 platform.
1. Turn off PowerShell access for all users except admins/allowed users.
This one is pretty straight forward. By default, O365 allows all users to have PowerShell access to the O365 API. This can be very dangerous because hackers can use this to create mailbox rules, send phishing emails, bypass 2-factor authentication, and forward emails to external addresses. This is not turning off PowerShell on the end user’s computer, it’s turning off the ability to access their O365 mailbox via PowerShell. Follow this guide by Microsoft on how to accomplish this: https://docs.microsoft.com/en-us/powershell/exchange/exchange-online/disable-access-to-exchange-online-powershell?view=exchange-ps
2. Turn off IMAP and POP3 if they are not used in your environment.
POP3 and IMAP are older email protocols and can be used to connect to Exchange mailboxes. The monitoring you get with O365 can show you events that happen in all of your user’s mailboxes. However, if an attacker sets up an email client and uses POP3 or IMAP the logging capabilities are reduced. This can help the hackers remain anonymous after they’ve compromised an account. https://blogs.technet.microsoft.com/praveenkumar/2017/06/09/how-to-diable-popimap-protocol-for-all-users-by-default-in-office-365/
3. Enforce modern authentication for all users
Turning on modern authentication can assist you with Single Sign On (SSO/SAML) and 2-factor capabilities. Here’s the how-to from Microsoft: https://support.office.com/en-us/article/enable-or-disable-modern-authentication-in-exchange-online-58018196-f918-49cd-8238-56f57f38d662
4. Disable OWA for users that don’t need access to it
Hackers use OWA after they’ve compromised an account in some cases. This allows them to do anything the compromised user can do in their mailbox. Create new emails, reply to emails, forward, setup signatures, and create rules are some of the most common things used by attackers. Disabling OWA for any user that doesn’t need it forces the hacker to setup the compromised account in Outlook or another email client to get access. Here’s the how-to: https://docs.microsoft.com/en-us/exchange/recipients-in-exchange-online/manage-user-mailboxes/enable-or-disable-outlook-web-app
5. Only allow inbound mail from your spam filter
Typically your MX records (mail record in DNS) are setup to deliver all emails to your spam filter’s IP address or domain name. If you don’t have an external spam filter then this doesn’t apply to you. If you have an external spam filter make sure to configure your mail flow rules to only allow email to be delivered from your spam filter’s IP address. Hackers can try to bypass your filter and send directly to Microsoft’s O365 cloud. If you have your spam filter setup as the only inbound mail connector and mail flow rules to do the same you can help mitigate this threat. See #5 link for configuring mail flow rules. Here’s how to create a connector: https://docs.microsoft.com/en-us/exchange/mail-flow-best-practices/use-connectors-to-configure-mail-flow/set-up-connectors-to-route-mail
6. Block logins from foreign countries
Creating Geo-Blocking rules is also a great tactic for account compromise mitigation. If the hacker compromises an account and is out of the country when they try to login, they will be blocked. Obviously the attacker can use a VPN or proxy to the US or whatever country you’re based in. At least this mitigation will slow them down a little more, helping you have a few extra minutes to fix the compromised account. https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition
7. Restrict O365/Azure API access to only allow connections from specific IP addresses
APIs have been getting hacked a bunch here lately. Be sure to check the settings on all of your APIs to ensure they’re not accepting connections from everyone on the internet. These should only allow connections from specific IP addresses that you specify. https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions
8. Block inbound emails to the “onmicrosoft.com” domain
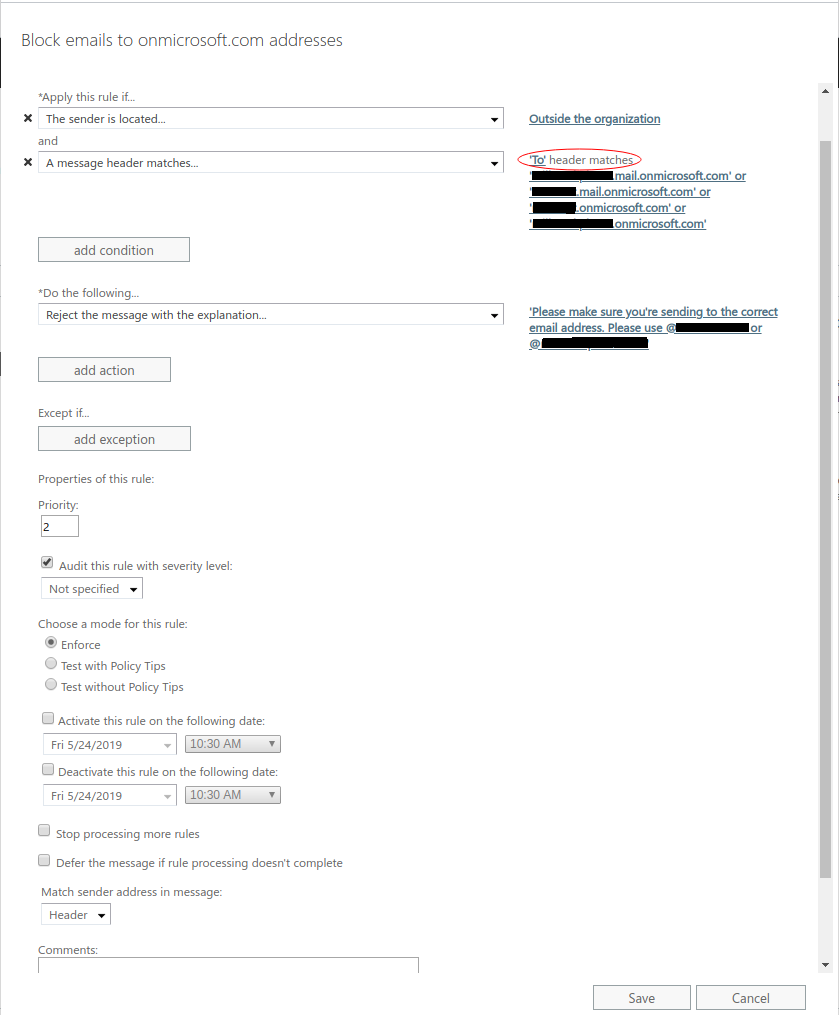
By default every new user in Office 365 is given a secondary email address with onmicrosoft.com appended to the end. For example user@yourdomain.onmicrosoft.com. The problem here is that you can’t control the onmicrosoft.com domain’s MX records to tell the email to go through the spam filter first. This allows hackers to completely bypass your spam filter and deliver phishing emails directly to your O365 environment. Block these inbound emails with a Mail Flow Rule configured in the Exchange Admin Console. Once in the console navigate to Mail Flow Rules. Create a new rule and add it to the top of the rule list. The single biggest thing to set when configuring this rule is the “To” Header Matches, yourdomain.onmicrosoft.com and yourdomain.mail.onmicrosoft.com. Wildcards don’t work unfortunately. Do this for each domain you have going into your O365 environment. A screenshot of these settings is at the bottom of this page.
Microsoft also came up with a guide for fixing compromised accounts. Check it out here: https://blogs.technet.microsoft.com/office365security/how-to-fix-a-compromised-hacked-microsoft-office-365-account/
These are just some of the most overlooked mitigations you can do in O365. Of course you’d want to have a spam filter, good password practices, 2-factor authentication, and other basic controls. These additional hardening steps can help create the most secure O365 environment you can. I’m sure there are other techniques that I’ve overlooked as well, but we’re always looking for new ways to lock it down. I’ll update this blog if I find any other mitigations.
Cyber:
https://www.scmagazine.com/massive-wordpress-redirect-campaign-spotted-targeting-tagdiv-themes-and-ultimate-member-plugins/article/790878/
New Intel chip flaw “Foreshadow” attacks SGX technology to extract sensitive data
https://thehackernews.com/2018/08/facebook-vpn-app-apple-store.html
Crypto:
https://www.coindesk.com/india-central-bank-forms-new-unit-to-tackle-blockchain-regulation/
https://www.coindesk.com/what-an-sec-bitcoin-etf-rejection-review-really-means/
https://www.coindesk.com/ethereum-call-leaves-pressing-questions-open-ahead-of-october-upgrade/
Follow me on Twitter: @eenglish34
https://itunes.apple.com/us/podcast/cyber-security-cryptocurrency-podcast-with-eric-english/id1414720078?mt=2#
Podcast: Play in new window | Download
Subscribe: RSS
Crypto:
https://www.coindesk.com/sec-rejects-7-bitcoin-etf-proposals/
https://www.coindesk.com/what-an-sec-bitcoin-etf-rejection-review-really-means/
Cyber:
T-Mobile Alerts 2.3 Million Customers of Data Breach Tied to Leaky API
Follow me on Twitter: @eenglish34
https://itunes.apple.com/us/podcast/cyber-security-cryptocurrency-podcast-with-eric-english/id1414720078?mt=2#
Podcast: Play in new window | Download
Subscribe: RSS
Cyber:
https://thehackernews.com/2018/08/apache-struts-vulnerability.html
http://www.ehackingnews.com/2018/08/canadian-telecom-providers-affected-by.html?utm_source=dlvr.it&utm_medium=twitter
Follow me on Twitter: @eenglish34
https://itunes.apple.com/us/podcast/cyber-security-cryptocurrency-podcast-with-eric-english/id1414720078?mt=2#
Podcast: Play in new window | Download
Subscribe: RSS
Crypto:
https://www.coindesk.com/sec-bitcoin-futures-etf/
https://www.coindesk.com/sec-faces-thursday-deadline-for-proshares-bitcoin-etf-decision/
https://www.coindesk.com/gemini-partners-with-3-crypto-exchanges-in-push-for-self-regulatory-org/
Cyber:
https://thehackernews.com/2018/08/mexico-banking-malware.html
https://thehackernews.com/2018/08/russia-election-hacking.html
https://thehackernews.com/2018/08/google-location-tracking.html
https://www.rapid7.com/globalassets/_pdfs/research/rapid7-threat-report-2018-q2.pdf
Follow me on Twitter: @eenglish34
https://itunes.apple.com/us/podcast/cyber-security-cryptocurrency-podcast-with-eric-english/id1414720078?mt=2#
Podcast: Play in new window | Download
Subscribe: RSS
Crypto:
https://www.polygon.com/2018/8/20/17760038/nvidia-geforce-rtx-2080-ti-2070-specs-release-date-price-turing
https://www.ccn.com/coinbase-trading-drops-83-since-january-offshore-cryptocurrency-exchanges-make-gains/
Cyber:
IoT botnet of heaters & ovens can cause massive widespread power outages
Follow me on Twitter: @eenglish34
https://itunes.apple.com/us/podcast/cyber-security-cryptocurrency-podcast-with-eric-english/id1414720078?mt=2#
Podcast: Play in new window | Download
Subscribe: RSS
Crypto:
https://www.engadget.com/2018/08/15/att-224-million-lawsuit-cryptocurrency-theft/
https://www.coindesk.com/30-of-uk-firms-hit-by-crypto-mining-malware-in-a-month-survey/
Cyber:
https://thehackernews.com/2018/08/foreshadow-intel-processor-vulnerability.html
Hundreds of reports of hacked Instagram accounts, possible Russian link
https://www.kb.cert.org/vuls/id/787952
http://www.ehackingnews.com/2018/08/flaw-in-amazon-echo-allows-hackers-to.html?utm_source=dlvr.it&utm_medium=twitter
Follow me on Twitter: @eenglish34
https://itunes.apple.com/us/podcast/cyber-security-cryptocurrency-podcast-with-eric-english/id1414720078?mt=2#
Podcast: Play in new window | Download
Subscribe: RSS